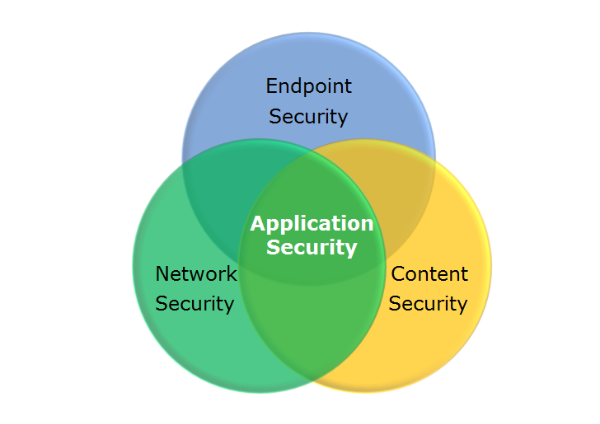
Services
We Provide A Wide Range Of Information Security Services
Passionate & Dedicated about information security on both a professional and personal level, and they are excited to do research which helps our clients and the organizations to be secure.
How We Can Help You?
Teamblue expert team of penetration testers simulates a real-world attack on your networks, applications, gadgets, and additionally individuals to exhibit the level of security in your infrastructure and effectively work upon the ways to take it to the next level. The comprehensive process begins with the ground breaking Open source intel gathering & enumeration and taken up to the next phase with appropriate exploitation techniques. We believe that every companies network and challenges are unique, so our security researchers prepare their methods and attack vectors for each engagement separately by analyzing it deeply.
Web-Application Security Testing Service - (WAST)
Our Web-Application Security Testing Service identifies technical and business logic vulnerabilities in your websites while providing you with detailed instructions and concrete recommendations. Integrated proprietary, open-source and commercial tools Intelligent automated testing engine selects the ideal combination of tools based on internal benchmarks Our reports provide step-by-step POCs and detailed fix information with code and config exmples Identifies both technical (OWASP Top 10, WASC 25, etc) and business logic vulnerabilities We create an in-depth map of your web-application business-logic and workflow Experts manually create specific test-cases for your web-application logic and workflow Access to our real-time security dashboard to track your projects, issues and fixes.

Vulnerability Assessment and Penetration Testing (VAPT)
Vulnerability Assessment is a process that scans for and identifies security holes within a network or communications infrastructure. Discovery is followed by prioritization of vulnerabilities and provision of guidelines for counter measures. Vulnerability Assessment. VAPT is an on-demand solution which makes it convenient to run tests over the Internet anywhere, anytime. It is a hybrid solution which blends automated testing with security expert analysis. This blended model provides the best quality test coverage while accelerating the test time. The unique technology identifies all possible attack vectors. The scope for each audit depends on the specific company, industry, compliance standards, etc.
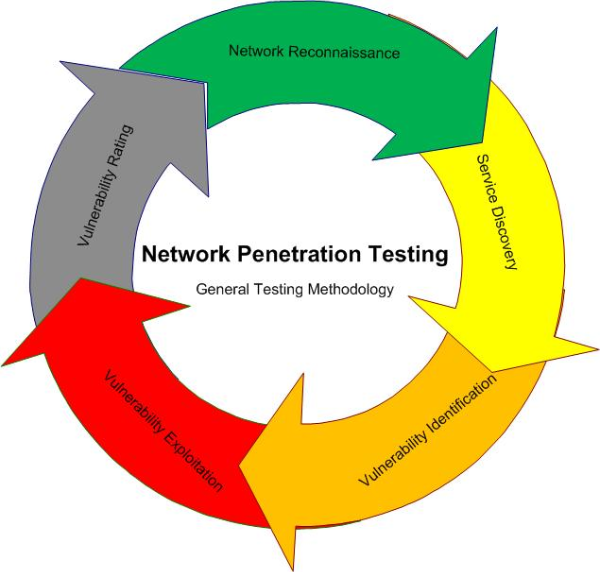
Network Penetration Testing
Network Penetration Test is an authorized hacking attempt designed to uncover and exploit network vulnerabilities and gain access to an organization’s information assets. The testing process is followed by a comprehensive report prioritizing vulnerabilities and outlining actionable mitigation strategies. It examines the security stance and procedures around. Network devices are commonly targeted by hackers in order to destabilize the entire network or to steal information. TeamBlue’s Network VAPT services help you validate the configuration of various technology devices & platforms on your network as the per best practices. We help you identify security issues and weak links in your network through network assessment, and penetration testing. Network Peneteration Testing can be of two types: Internal NPT and External NPT. Internal NPT would want the experts to come to their organization and do the Penetration Testing where the External one would not require a physical access but, could also be done by providing the virtual access. External NPT could be done even from different countries for different countries since it's all about accessing the network virtually without the physical access.
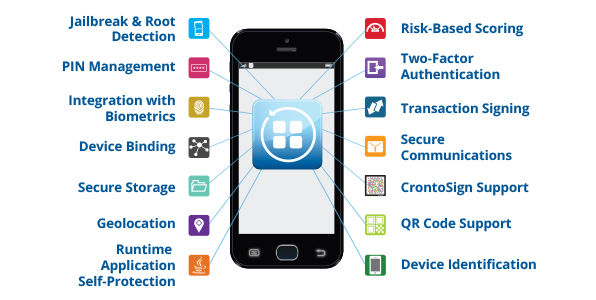
Mobile Application Security Testing
Annual Website Security Management Service - AWSM

DDOS Mitigation
Who We've Worked With













